Configure Network Proxy Settings
Topics covered in this article:
- How To Arrange A Proxy Server In Internet Explorer
- Permalink To "yarn Configuration"
- Proxy
- Tips On How To Share Your Mac Web With An Iphone
- Connect
- What Proxy Setting Ought To I Use? High Three Use Instances
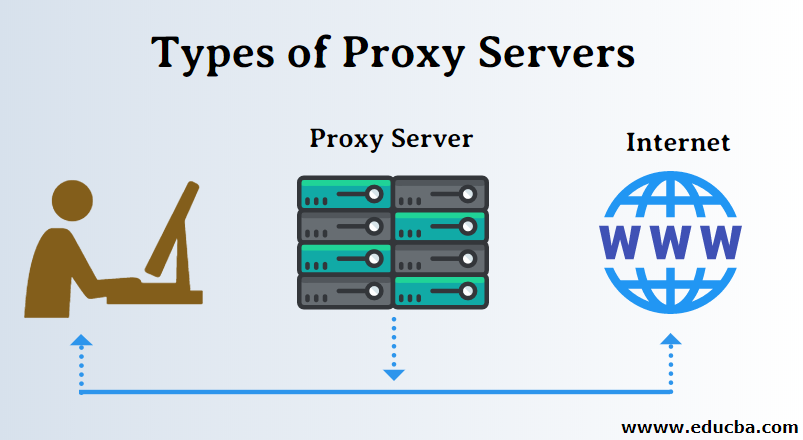
Because a proxy server has its own IP address, it acts as a go-between for a pc and the web. FortiProxy helps to reduce bandwidth calls for and optimize the network with content and video caching. You can set the Address and the Port for a proxy server with the option to bypass it for native addresses.
5) Type the proxy settings provided by your community administrator. 4) If the network has no proxy settings, touch “None” under “Proxy”, then touch “Manual” in the pop-up menu. After inputting the small print, you would have to authenticate the proxy server. You would want this authentication if you are not utilizing the whitelist IP technique.
The Way To Set Up A Proxy Server In Internet Explorer
To get began with a proxy server, you want to configure it in your pc, gadget, or community. Each working system has its personal setup procedures, so examine the steps required for your computer or community. Some network administrators require you to join with inside or exterior community sources via a proxy server. By default, the Wi-Fi networks aren't configured to connect by way of a proxy, but you need to use the following steps to change that for each Wi-Fi community you’ve added. If you do not use a proxy server, go away this subject empty. If you employ a proxy, ensure the handle and port info in this area match the knowledge in your browser settings.
This requirement could be necessary for organizations that are topic to various privateness laws similar to PCI, HIPAA, or SOX. Turn on the “use a proxy server” toggle/ examine box which can mechanically activate the system proxy settings textual content fields. If your whole functions want to use the same proxy, you might need to use a default proxy configured at the Operating System level.
Permalink To "yarn Configuration"
This will stop malicious individuals from attacking your gadgets. As we all know, cybercriminals have one main aim in thoughts; steal knowledge. If you are reading this, in all probability you're looking for the extra privateness and security wanted while shopping on-line. Chrome proxy settings will make your searching much more secure and personal.
Who would use a proxy server?
A proxy server is a system or router that provides a gateway between users and the internet. Therefore, it helps prevent cyber attackers from entering a private network. It is a server, referred to as an “intermediary” because it goes between end-users and the web pages they visit online.
This examines the data going out and in of your pc or community. It then applies rules to prevent you from having to reveal your digital tackle to the world. Only the proxy’s IP tackle is seen by hackers or different dangerous actors.
Proxy
The primary benefit of a shared proxy is its low price. Because they are shared by others, you might get blamed for somebody else’s dangerous selections, which could get you banned from a website. A residential proxy offers you an IP address that belongs to a specific, bodily device.
AdTheorent Highlights Achievements Since Mid-Year 2021 2021-12-17 Press Releases - Stockhouse
AdTheorent Highlights Achievements Since Mid-Year 2021 2021-12-17 Press Releases.
Posted: Fri, 17 Dec 2021 12:19:39 GMT [source]
Select the kind of network you utilize, which is normally Ethernet or Wi-Fi. To access the Windows Settings menu, press the Windows + I keys concurrently. Press the Windows + I keys concurrently to entry the Windows Settings menu. Please stand by, whereas we're checking your browser... Chris Hoffman is Editor-in-Chief of How-To Geek.
How To Share Your Mac Web With An Iphone
We have thousands of articles and guides that will help you troubleshoot any concern. Our articles have been learn over a hundred and fifty million instances since we launched in 2008. [newline]A distorting proxy identifies itself as a proxy to a web site however hides its personal id. It does this by altering its IP tackle to an incorrect one.
These settings may cause problems with VPNs and may be disabled when you encounter issues; otherwise, depart them on. When setting this object, all properties are elective. Note that any properties that are omitted shall be reset to their default worth. Note that in distinction to a shell script in /etc/profile.d described in the next section, the /etc/environment file is NOT a shell script and applies to all processes and not using a shell. Define the setting https://articlescad.com/what-is-a-web-proxy-address-1073494.html variables in /etc/environment file if you want to add a everlasting proxy within the CentOS/RHEL 7.
If you need reliable safety and encryption for your web site visitors, contemplate a VPN. Avast SecureLine VPN hides your data from snoopers and protects your online identity, and it is also much simpler to arrange than a proxy server. To allow automated proxy detection, select “Auto”. This characteristic is usually used on business and college networks. If your present network doesn’t present proxy particulars using the WPAD protocol, your iPhone or iPad won’t use a proxy, even if you choose “Auto” here.
I see what is happening now. The operation name field does not exist - it's not meant to. If you configure the integration as a proxy (default), you need to route based on two properties of the event, the path and the httpMethod. httpMethod will contain the verb (GET/POST/etc)
— Stefano Buliani (@sapessi) April 30, 2021
This article describes how to configure the proxy settings in Postman to direct all requests made in Postman to route through a proxy server. This is completely different from capturing community visitors with the built-in proxy which permits Postman to intercept community traffic. A proxy server supplies a gateway between community customers and the web.
What Proxy Setting Should I Use? Top Three Use Instances
If you have a Proxy Auto-Config file, choose Proxy Auto-Config and Android will immediate you to enter the PAC tackle. Please keep in mind that Internet Explorer is an outdated net browser. Instead, switch to a browser that’s still receiving common updates and help, similar to Avast Secure Browser, Chrome, Edge, Firefox, or Safari. Though since quite a few individuals and companies still use Internet Explorer , you want to know tips on how to set issues up when needed.
To configure Tableau Server, you employ the tsm configuration set command. The data you have to acquire corresponds to options you may need if you run tsm. Tableau Desktop and Tableau Prep do not support authentication with a reverse proxy. For remote entry, use a VPN resolution or configure your reverse proxy to route visitors from Tableau Desktop or Tableau Prep on to Tableau Server for authentication. A reverse proxy can be utilized to protect an organization's many net servers towards internet application vulnerabilities. Additionally, the reverse proxy provides other benefits similar to server concealment and enhanced performance.
Instead, we advise you learn how to set up a proxy server on Windows, MacOS, and the most well-liked web browsers. The proxy settings you configure are unique to each Wi-Fi community. That’s as a end result of you http://www.thefreedictionary.com/buy shared proxy may need to make use of a proxy whereas connected to the Wi-Fi network at your office, however not at http://dedicatedsocks5tjas667.unblog.fr/2021/04/02/what-does-configure-proxy-mean-for-wifi/ residence or on other Wi-Fi networks. If you might have configured authentication at the proxy server gateway, then your proxy server must reply to Tableau Mobile HTTP requests with a HTTP 302 response. The 302 should embrace a redirect to the id supplier login web page. To view a diagram that describes the 302 authentication sequence, see Tableau Mobile Authentication Sequence within the Tableau Community.
Configuring Internet Explorer to work with Burp - The Daily Swig
Configuring Internet Explorer to work with Burp.
Posted: Mon, 06 Sep 2021 13:30:06 GMT [source]
Support for this script is identical as described beneath underneath Automatic Proxy Configuration. To automatically configure your proxy server settings, choose Auto Proxy Discovery. Type in the proxy server address and its port quantity in the fields on the right. You have plenty of choices in relation to web privateness. There’s so much to learn, similar to understanding what a reverse proxy is or distinguishing between VPNs, proxies, and Tor.
Define Proxy Settings
There are many proxies, every with a special objective. Check out this listing of the commonest proxies in use today. Double-clicking this .bat file should open Postman without any of the proxy environment variables set. Double-clicking this bat file should open Postman with none of the proxy surroundings variables set. Postman's native apps for Mac, Windows, and Linux assist configuring proxies.
How to set up a VPN for increased security and privacy - The Verge
How to set up a VPN for increased security and privacy.
Posted: Thu, 10 Jun 2021 07:00:00 GMT [source]
Tableau Server http://buyprivatesocks5axqc752.huicopper.com/what-is-an-open-proxy-ip-address was designed to operate inside a protected inner community. Do not arrange Tableau Server immediately on the web or in a DMZ. Instead, communications between your community and the web should be mediated using proxy servers. Forward proxy servers mediate traffic from contained in the community to targets on the web.
Should I change the DNS on my router?
By default, your router uses your Internet service provider's DNS servers. If you change the DNS server on your router, every other device on your network will use it. Really, if you want to use a third-party DNS server on your devices, we recommend you just change it on your router.
When you utilize a public proxy, you also run an elevated risk of getting your data accessed by others on the internet. When a computer connects to the web, it uses an IP tackle. This is similar to your home’s road tackle, telling incoming knowledge the place to go and marking outgoing knowledge with a return tackle for different gadgets to authenticate. A proxy server is basically a computer on the internet that has an IP handle of its own.
What happens when you turn on VPN on iPhone?
A.
Once VPN is enabled, your iPhone creates a secure and encrypted tunnel to the fortified VPN servers and all traffic between the two is kept hidden from the local ISPs and Public Wi-Fi networks. As the connection is encrypted, they are unable to intercept any data or invade your privacy.
Furthermore, click here to be taught more about Firefox proxy set up, too. Configuring a proxy is an important step for internet security and privacy. Though some advocate a ‘one dimension fits all strategy to proxy settings, tailoring your proxy to your particular use case can maximize safety and performance. You can choose or unselect the option "Use the system proxy" to enable or disable the system proxy. When it's unchecked, all of the requests are made immediately.